The combined count of apps available on the Apple App Store and Google Play Store is over 5 million. The explosion of developers and the latest apps being launched every day have also escalated the cyber security risks for mobile application. According to a research report by Gartner, more than 75 percent of the mobile apps fail the basic security tests.
Technological advancements have ballooned the figure of smartphone users. The number is poised to surpass the 5 billion mark this year only. Smartphones have made our lives easier, but it has also become a comfortable space for cyber criminals. They are stealing data, leaking sensitive information in the public domain, and trying to cripple the whole ecosystem of smartphones.
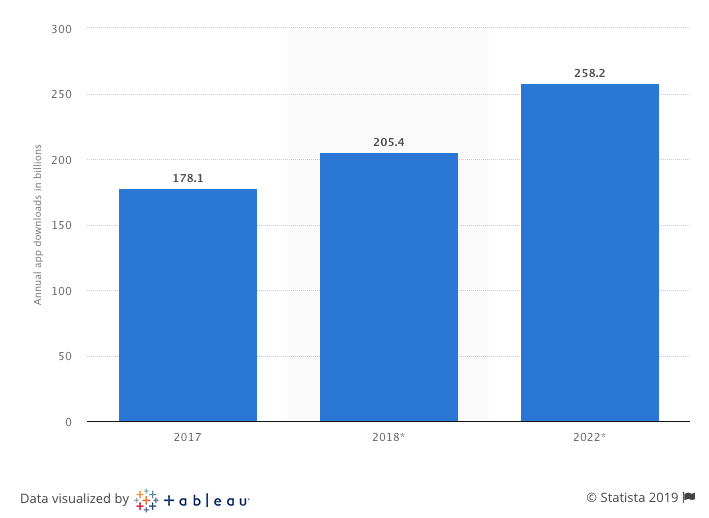
Cyber criminals are also having a ball as the number of mobile mobile app downloads is increasing exponentially.
The goldmine of user data, including banking, contact details, and passwords are readily available to hackers. They are also able to access credit cards, emails, and personal information very quickly if you are using a poorly secured mobile application.
With everything accessible on these mobile apps, they have become more prone to advanced and sophisticated cyber-attacks. A single cyber-attack can trivialize your business interests and expose your user data to anyone in the world.
But before talking about the strategy to secure mobile apps against cyber threats, it is imperative to talk about the major types of cyber-security threats.
Major Cyber Security Threats
1. Cross-Device Cyber Threat
Cross-device threats occur when apps let smartphone users download the application from the computer first and later to a smartphone device.
2. App Store Security
More than 90 percent of mobile apps are prone to cyber-security threats. Android gadgets are more prone to such cyber-attacks as they cater to a massive range of devices, operating system needs, and app store checks. Apple is much safer as it controls all the hardware and also offers greater access to the level of apps.
3. IoT Hardware
IoT devices are meant to collect user data and leverage it for smart decision making. However, Android allows the machine to establish connections with other operating systems. This process increases security and can get out of hand at any point in time.
4. Mobile Malware
Mobile gadgets are always prone to Trojan attacks, spy-wares, viruses, and malware. These are straightforward means for hackers to steal the data.
5. Illegal Access
Your all digital accounts, including bank, social media, email, and other applications, are always exposed to unauthorized access.
6. Single Device for Multiple Purposes
People at the corporate level always deal with sensitive and private information. This high-risk data is always susceptible to the risk of getting mixed with personal data if employees do everything on the same device.
Any kind of breach in the mobile app’s security can be catastrophic for both business owners and developers.
Hence, you need to be on your toes to tackle advanced cyber-security threats to keep your app safe from hackers.
How to protect your Mobile Applications Against Dangerous Cyber Threats?
1. Design for App Security
Now, when you have decided to ensure end-to-end security of your app, you should start by preparing the threat model from the starting. The best approach should be brainstorm like a hacker to identify all the loopholes. It will help you enforce ironclad security measures. You can also take the assistance of professional security guys who act like hackers to test the level of security and identify all the vulnerabilities.
The security of the app becomes even more critical when you want to run an eCommerce business through it. Just imagine about the possibility of the app getting hacked and sensitive user data, including phone number, bank account numbers, and credit details floating all over cyberspace. Your most important priority should be to safeguard sensitive user data at any cost.
2. Mobile Device Management
Online security of the app depends mostly on the kind of device being used by the user. iOS and Android, both operating systems behave differently – and you need to have different approaches for each OS to ensure adequate security. Developers should know the fact that the data accumulated on any device is capable of causing a security breach.
And this is where encryptions methods including 256-bit Advanced Encryption Standard, come into play. It helps you keep the data secure in the form of database, file, and other data formats. Moreover, while finalizing the mobile app cyber-security, it is imperative to consider encryption key management.
When we consider Apple, it has enforced strict security policy in place. It allows app owners to prevent any user from installing the app if they feel that the security of the user’s device is already breached.
Mobile Device Management: iOS Vs Android
iOS devices can be managed efficiently by taking the assistance of Mobile Device Management (MDM) or Enterprise Mobile Management (EMM) product. Other vendors who provide the same facility include MobileIron, Good Technology, and MaaS360, among others. Aside from this, you can also take the services of Microsoft Exchange ActiveSync Protocol, which is a cheap but efficient policy management tool
Android devices, on the other hand, are a bit notorious when it comes to managing and preventing security threats. One of the primary reasons they are prone to security breaches is their cheap hardware. It is advisable to only use Android for Work (A4W) in the business environment. This encrypted version of the Android separates professional and personal mobile applications in two separate categories.
3. App Wrapping
App Wrapping segregates your mobile application from the remaining devices by capturing it in a safe zone. Developers who are using MDM provider get this option automatically. By setting a few parameters, you can segment the app without writing any code.
4. Secured User Authentication
Deploying secured user authentication and authorization is essential for any mobile application’s security. It is crucial to establish the fact that a genuine user is running the app to prevent its access from hackers and malware.
While setting up the user authentication, you must ensure including all the essential privacy points, identity, session management, and mobile security features. 2FA (two-factor authentication) or an MFA (multi-factor authentication) should be enforced for stronger user authentication.
5. Hardening the OS
There are several methods to harden the operating system for added security of your mobile app. Apple has been the torchbearer of enforcing ironclad security features with iOS. For iOS app’s safety, you need to stay updated by reading the quarterly reviews of Apple’s security guide, stay updated about the latest code samples, and understand static code commercial tools.
6. Ensure Security of APIs
Always ensure to leverage APIs to handle all the data and business logic of the mobile app. APIs ensure the security of data at any state including at transit or remaining static. It is one of the most features of any mobile app.
Deploy SSL with 256-bit encryption to ensure the security of data in transit. And for data at rest, you can secure the origin and device both. Also, make sure to deploy APIs which have an app-level authentication. Keep sensitive data gated to the memory and ensure the authorized person is only using the services.
7. Hire a Professional
Isn’t it obvious? If the above-mentioned points are giving you a headache, then you can always hire cybersecurity professionals to help you fight the menace of cyber-threats. Most credible cyber-security experts have a Master Certificate in Cyber Security and extensive experience in subverting the major security threats.
Hiring an expert may come with a hefty price tag, however, in the end, it will be well worth the effort. The best part is that you don’t have to track the potential threats or tweak anything on your own; the professional you hire will assist you from the beginning until the very end.
Here are some of the skills that the cyber security expert should have in his/her resume:
- Adept at mobile device management
- In-depth understanding of network architecture
- Ability to detect potential cyber threats, such as unauthorized access, data breach, etc.
- Should demonstrate the ability to predict security intrusions
- Strong collaboration skills and the ability to work with fellow team-members
Summing it up
Remember, before you go about securing your mobile apps against dangerous cyber security threats, it is crucial to identify what potential threats you are fighting against. After all, you can’t find a solution without understanding the gist of the problem in the first place.
Once you identify the security threats plaguing your mobile app, it will be decidedly easier for you to tackle the real threat.
If you fail to follow through the above practices to avoid mobile security threats, you might end up losing your confidential data, resulting in heavy losses. So, don’t delegate anymore and work towards subverting cyber crime today.
Looking for the most safe and secure apps?
Are cyber threats keeping you awake at night. Get in touch with us and our highly experienced developers will help create an app with ironclad security and top-notch safety.
Click here to book a free consultation today.